What delimiter is used in a flat file for running flat-file trusted reconciliation? (Choose the best answer.)
- A. , (comma)
- B. | (pipe)
- C. : (colon)
- D. The delimiter is configurable.
Answer : B
Reference:http://www.oracle.com/webfolder/technetwork/tutorials/obe/fmw/oim/10.1.4/oim/ obe12_using_gtc_for_reconciliation/using_the_gtc.htm
What configuration must be defined for Oracle Identity Manager (OIM) access policies to be reevaluated automatically for existing affected users? (Choose the best answer.)
- A. The “Disable if no longer applied” flag needs to be checked.
- B. The “Evaluate User Policies” scheduled job needs to be scheduled.
- C. The “Revoke if no longer applied” flag must be checked.
- D. The “Retrofit” flag must be checked in the policy definition.
Answer : B
Reference:http://docs.oracle.com/cd/E27559_01/admin.1112/e27149/scheduler.htm#OMA
DM787 -
You are deploying connectors on Oracle Linux systems. As part of the process, you must create a new directory in the target system that will be used by the connector when interfacing with Oracle Identity Governance and the/etc/passwordand/etc/shadowfiles.
Identify the goal of this directory, and explain how Oracle Identity Manager uses that access.(Choose the best answer.)
- A. Create a directory on the target system where the connector can log events. The default directory is/var/logs/oim/connectors.
- B. Create a directory on the target system where the connector can create mirror files for the/etc/passwordand/etc/shadowfiles. This directory is specified in themirrorFilesLocationentry of theLookup.UNIX.Configurationlookup definition. The default value is/etc/connector_mirror_files.
- C. Create a directory on the target system where the connector can store temporary files when running the reconciliation process. These files will be stored until the reconciliation is completed. The default directory is/var/oim/temp/connectors.
- D. Create a directory on the target system where the connector can create backup files for the/etc/passwordand/etc/shadowfiles. Thisdirectory is specified in themirrorFilesLocationentry of theLookup.UNIX.Configurationlookup definition. The default value is/etc/connector_backup_files.
Answer : D
Reference:https://docs.oracle.com/cd/E22999_01/doc.111/e17694/custom.htm#CGUNX21
Which statement is true about implementing attribute-level security for user attributes in
Oracle Identity Manager (OIM)? (Choose the best answer.)
- A. The authorization policy for user-defined fields (UDFs) is inherited from its parent object and cannot be changed.
- B. When a new user-defined field (UDF) is added, the User Viewer policy must be changed to allow view permission.
- C. To restrict an attribute from being seen or modified, you change its policy in OES and include the attribute in the deny list.
- D. When a new user-defined field (UDF) is added, the User Administrator policy must be changed to allow view permission.
- E. The authorization policy for user-defined fields (UDFs) is inherited from its parent object and also includes the UDF in the deny list.
Answer : B
R2 enables multiple users to create customizations by
using multiple sandboxes.
How can you avoid conflicts between thesemultiple sandboxes intended for publishing?(Choose the best answer.)
- A. Create one sandbox per user.
- B. Activate the sandbox and publish content before deactivation.
- C. Work on distinct artifacts in each sandbox.
- D. Use one sandbox per user and request changes to xelsysadm.
Answer : A
Reference:http://docs.oracle.com/cd/E27559_01/dev.1112/e27150/uicust.htm#OMDEV479
Which statement is true about the check-in and check-out capabilities in Oracle Privileged
Account Manager (OPAM)? (Choose the best answer.)
- A. Authorized users can check out an account, which provisions it; they can then check in the account, which de-provisions it.
- B. Authorized and non-authorized users can check in an account, which provisions it; they can then check out the account, which de-provisions it.
- C. Authorized users can check out an account before using it; they can then check in the account when they are finished with it.
- D. Authorized and non-authorized users can check out an account before using it; they can then check in the account when they are finished with it.
- E. Authorized users can check out an account before using it, but administrators must check in the account.
Answer : C
Explanation:
Oracle Privileged Account Manager requires all authorized users to check out an account before using it, and then to check that account back in when they are finished with it.
Oracle Privileged Account Manager audits account check outs and check ins by tracking the real identity (the person's name) of every shared administrator user at any given moment in time. By using this information, Oracle Privileged Account Manager can provide a complete audit trail that shows who accessed what, when, and where.
Reference:https://docs.oracle.com/cd/E27559_01/admin.1112/e27152/und_opam.htm#OP
MAG114 -
As a system administrator, you deploy Oracle Privileged Account Manager and want toproceed with OVD and OPAM integration. But you are unable to log in to the console to proceed with the configuration.
Identify the role that you need to log in to the console. (Choose the best answer.)
- A. Security Administrator Admin role
- B. Application Configurator Admin role
- C. User Manager Admin role
- D. System Configurator Admin role
Answer : A
View the Exhibit.
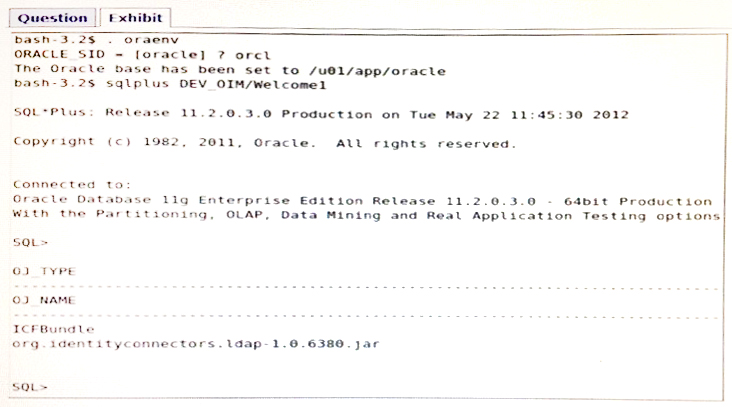
You have installed a connector, and you want to confirm that the connector library is loaded into the Oracle Identity Manager database. Identify the query that produces the results in the Exhibit.(Choose the best answer.)
- A. select OJ_TYPE,OJ_NAME from OIMLIB_JARS;
- B. select OJ_TYPE,OJ_NAME from OIMHOME_JARS;
- C. select OJ_TYPE,OJ_NAME from OIM_JARS;
- D. select OJ_TYPE,OJ_NAME from OIMCONNECTOR_JARS;
- E. select OJ_TYPE,OJ_NAME from OIMLIBRARY_JARS;
Answer : B
A customer wants the ability to approve or reject requests from the approval notification itself. What option or component should you configure to enable this feature through SOA composite application?(Choose the best answer.)
- A. With the SOA composite tool, add input parameters for the Human Task. Then click the Add icon and add a string parameter called Notification. Set the parameter as the following data type: {http://xmlns.oracle.com/request/NotificationActionalbe}OtherDetails
- B. Set up a new Oracle business rule called Notification and set the Then action as follows:CallNotificationActionableResource(User : Null, Groups : Manager, Environment Owner, Response Type: required, ruleName: Rule1, list:List)
- C. With the SOA composite tool, select the Approval Human Task from your workflow and click Notification. Specify when you want a notification message to be sent to the assignee or requester, and then make the notification actionable.
- D. With the SOA composite tool, add input parameters for the Human Task. Then click the Add icon and add a string parameter called Notification. Set the parameter as the following data type: {http://xmlns.oracle.com/request/RequestDetails}OtherDetails
Answer : C
You are doing an initial load of all the directory groups into the catalog in Oracle Identity
Manager. What must be configured in the Catalog Synchronization job for this purpose?
(Choose the best answer.)
- A. Process Entitlements parameter is checked.
- B. Process Roles parameter is checked.
- C. Both Process Application Instances parameter and Process Entitlements parameter are checked.
- D. Both Process Application Instances parameter andProcess Roles parameter are checked.
- E. File Path parameter is used.
Answer : D
Which two statements describe how Oracle Privileged Account Manager (OPAM) integrates with target systems? (Choose two.)
- A. OPAM uses Identity Connector Framework (ICF) connectors, but they must be modified to support OPAM.
- B. OPAM uses out-of-the-box Identity Connector Framework (ICF) connectors.
- C. OPAM can use customer-created, Identity Connector Framework (ICF) compliant connectors.
- D. OPAM cannot use customer-created, Identity Connector Framework (ICF) compliant connectors.
- E. OPAM cannot use Identity Connector Framework (ICF) compliant connectors; new OPAM connectors must be developed for each application.
Answer : C,E
Reference:http://docs.oracle.com/cd/E40329_01/admin.1112/e27152/get_started.htm#OP
MAG31231 -
Which statement is true about the initial configuration of network connections for Oracle
Privileged Account Manager (OPAM)? (Choose the best answer.)
- A. Network connections to the target system using the Identity Connector Framework (ICF) must always be encrypted, and Oracle requires using secured channels for this.
- B. Network connections to the target system using the Identity Connector Framework (ICF) can be either encrypted or clear text, and Oracle recommends using secured channels for this.
- C. Network connections to the End User Interface use Oracle Identity Navigator and are always encrypted.
- D. Network connections to the End User Interface use Oracle Enterprise Manager and are always encrypted.
- E. Network connections to the End User Interface use x.509 certificates and are always encrypted.
Answer : C
R2. The first step is to change the company logo in the upper-left corner. You obtain the image URL link that points to the company logo webpage.
Specify the code to enter in the Background Image field in the section edit window.(Choose the best answer.)
- A. url{http://companywebpage.com/img/logo.gif}
- B. url[http://companywebpage.com/img/logo.gif]
- C. http://companywebpage.com/img/logo.gif
- D. url(http://companywebpage.com/img/logo.gif)
- E. url{(http://companywebpage.com/img/logo.gif)}
Answer : D
Reference:http://docs.oracle.com/cd/E27559_01/dev.1112/e27150/uicust.htm#OMDEV274
2(see step 8)
You have created anOperational Levelapproval policy for a request to be raised by a user
R2. This request type is set asSelf Request Resourceand
needs to be approved by the manager of the user who raised the request. What two approval processes can be used for this case? (Choose two.)
- A. default/RequesterManagerApproval!1.0
- B. default/BeneficiaryManagerApproval!1.0
- C. default/ManagerApproval!1.0
- D. default/DefaultRoleApproval!1.0
- E. default/DefaultApproval!1.0
Answer : A,E
R2 after -
LDAP sync is enabled? (Choose the best answer.)
- A. LDAP sync must be configured when Oracle Identity Manager is installed.
- B. This is done through a scheduled job in Oracle Identity Manager.
- C. The users and roles need to be created manually in the LDAP provider.
- D. This is done automatically after LDAP sync is enabled.
Answer : B
Reference:https://docs.oracle.com/cd/E27559_01/integration.1112/e27123/oid_oim.htm#ID
MIG4362 -

