What can an administrator do if a client has been incorrectly Period Blocked?
- A. Disconnect the client from the network
- B. Manually release the IP from the temporary Blacklist
- C. Nothing, it is not possible to override a Period Block
- D. Force a new IP address to the client. B
Answer : Explanation
Reference: http://help.fortinet.com/fweb/581/Content/FortiWeb/fortiweb-admin/monitor_blocked_ips.htm
When generating a protection configuration from an auto learning report what critical step must you do before generating the final protection configuration?
- A. Restart the FortiWeb to clear the caches
- B. Drill down in the report to correct any false positives.
- C. Activate the report to create t profile
- D. Take the FortiWeb offline to apply the profile B
Answer : Explanation
How does an ADOM differ from a VDOM?
- A. ADOMs do not have virtual networking
- B. ADOMs improve performance by offloading some functions.
- C. ADOMs only affect specific functions, and do not provide full separation like VDOMs do.
- D. Allows you to have 1 administrator for multiple tenants D
Answer : Explanation
You are configuring FortiAnalyzer to store logs from FortiWeb.
Which is true?
- A. FortiAnalyzer will store antivirus and DLP archives from FortiWeb.
- B. You must enable ADOMs on FortiAnalyzer.
- C. To store logs from FortiWeb 5.6.0, on FortiAnalyzer, you must select "FoкtiWeb 5.4".
- D. FortiWeb will query FortiAnalyzer for reports, instead of generating them locally. B
Answer : Explanation
Reference:
https://docs.fortinet.com/uploaded/files/3143/FortiAnalyzer-5.4.1-Administration-Guide.pdf page 19
Which of the following would be a reason for implementing rewrites?
- A. Page has been moved to a new URL
- B. Page has been moved to a new IP address
- C. Replace vulnerable functions.
- D. Send connection to secure channel A
Answer : Explanation
A client is trying to start a session from a page that should normally be accessible only after they have logged in.
When a start page rule detects the invalid session access, what can FortiWeb do? (Choose three.)
- A. Reply with a "403 Forbidden" HTTP error
- B. Allow the page access, but log the violation
- C. Automatically redirect the client to the login page
- D. Display an access policy message, then allow the client to continue, redirecting them to their requested page
- E. Prompt the client to authenticate ABC
Answer : Explanation
Which is true about HTTPS on FortiWeb? (Choose three.)
- A. For SNI, you select the certificate that FortiWeb will present in the server pool, not in the server policy.
- B. After enabling HSTS, redirects to HTTPS are no longer necessary.
- C. In true transparent mode, the TLS session terminator is a protected web server.
- D. Enabling RC4 protects against the BEAST attack, but is not recommended if you configure FortiWeb to only offer TLS 1.2.
- E. In transparent inspection mode, you select which certificate that FortiWeb will present in the server pool, not in the server policy. ACE
Answer : Explanation
When viewing the attack logs on your FortiWeb, which IP Address is shown for the client when using XFF Header rules?
- A. FortiGate"™s public IP
- B. FortiGate"™s local IP
- C. FortiWeb"™s IP
- D. Client"™s real IP D
Answer : Explanation
Which of the following is true about Local User Accounts?
- A. Must be assigned regardless of any other authentication
- B. Can be used for Single Sign On
- C. Can be used for site publishing
- D. Best suited for large environments with many users A
Answer : Explanation
In which operation mode(s) can FortiWeb modify HTTP packets? (Choose two.)
- A. Transparent Inspection
- B. Offline protection
- C. True transparent proxy
- D. Reverse proxy D
Answer : Explanation
Reference: http://help.fortinet.com/fweb/541/Content/FortiWeb/fortiweb-admin/planning_topology.htm
What other consideration must you take into account when configuring Defacement protection?
- A. Use FortiWeb to block SQL Injections and keep regular backups of the Database
- B. Also incorporate a FortiADC into your network
- C. None. FortiWeb completely secures the site against defacement attacks
- D. Configure the FortiGate to perform Anti-Defacement as well D
Answer : Explanation
Under what circumstances would you want to use the temporary uncompress feature of FortiWeb?
- A. In the case of compression being done on the FortiWeb, to inspect the content of the compressed file
- B. In the case of the file being a .MP3 music file
- C. In the case of compression being done on the web server, to inspect the content of the compressed file.
- D. In the case of the file being an .MP4 video C
Answer : Explanation
What is one of the key benefits of the FortiGuard IP Reputation feature?
- A. FortiGuard maintains a list of public IPs with a bad reputation for participating in attacks.
- B. It is updated once per year
- C. Provides a Document of IP addresses that are suspect, so that administrators can manually update their blacklists
- D. It maintains a list of private IP addresses A
Answer : Explanation
You are deploying FortiWeb 5.6.0 in an Amazon Web Services cloud. Which 2 lines of this initial setup via CLI are incorrect? (Choose two.)
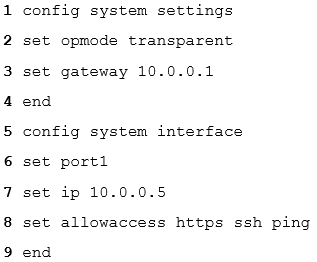
- A. 6
- B. 9
- C. 3
- D. 2 AC
Answer : Explanation

