Your network contains an Active Directory domain. All servers run Windows Server 2008
R2 and are members of the domain. All servers are located in the main office.
You have a portable computer named Computer1 that runs Windows 7. Computer1 is joined to the domain and is located in a branch office.
A file server named Server1 contains a shared folder named Share1.
You need to configure Computer1 to meet the following requirements:
-> Minimize network traffic between the main office and the branch office
-> Ensure that Computer1 can only access resources in Share1 while it is connected to the network.
What should you do?
- A. On Computer1, enable offline files.
- B. On Computer1, enable transparent caching.
- C. On Server1, configure DirectAccess.
- D. On Server1, configure Share1 to be available offline.
Answer : B
Explanation:
Transparent Caching -
When you enable transparent caching, Windows 7 keeps a cached copy of all files that a user opens from shared folders on the local volume. The first time a user opens the file, the file is stored in the local cache. When the user opens the file again, Windows 7 checks the file to ensure that the cached copy is up to date and if it is, opens that instead. If the copy is not up to date, the client opens the copy hosted on the shared folder, also placing it in the local cache. Using a locally cached copy speeds up access to files stored on file servers on remote networks from the client. When a user changes a file, the client writes the changes to the copy of the file stored on the shared folder. When the shared folder is unavailable, the transparently cached copy is also unavailable. Transparent caching does not attempt to keep the local copy synced with the copy of the file on the remote file server as the Offline
Files feature does. Transparent caching works on all files in a shared folder, not just those that you have configured to be available offline.
Which of the following is not a rating for games in Windows 7?
- A. General Audience (G)
- B. Everyone (E)
- C. Teen (T)
- D. Adults Only (AO)
Answer : A
You start a computer by using Windows Preinstallation Environment (Windows PE).
You need to dynamically load a network adapter device driver in Windows PE.
What should you do?
- A. Run Peimg.exe and specify the device driver path.
- B. Run Drvload.exe and specify the device driver path.
- C. Run Winpeshl.exe and specify a custom Winpeshl.ini file.
- D. Run Wpeutil.exe and specify the InitializeNetwork command.
Answer : B
Explanation:
Drvload -
The Drvload tool adds out-of-box drivers to a booted Windows PE image. It takes one or more driver .inf files as inputs. To add a driver to an offline Windows PE image, use the peimg tool.NOT WinpeshlWinpeshl.ini controls whether a customized shell is loaded in
Windows PE instead of the default Command Prompt window. To load a customized shell, create a file named Winpeshl.ini and place it in %SYSTEMROOT% \System32 of your customized Windows PE image. The .ini file must have the following section and entry.NOT
WpeutilThe Windows PE utility (Wpeutil) is a command-line tool that enables you to run various commands in a Windows PE session. For example, you can shut down or restart
Windows PE, enable or disable a firewall, set language settings, and initialize a network.
You have a computer that runs Windows 7.
You need to configure the computer to download updates from a local Windows Server
Update Services (WSUS) server. What should you do?
- A. From Windows Update, modify the Windows Update settings.
- B. From the local Group Policy, modify the Windows Update settings.
- C. From the System settings, modify the System Protection settings.
- D. From the local Group Policy, modify the Location and Sensors settings.
Answer : B
Which of the following is not a volume type usable by Windows 7?
- A. FAT
- B. exFAT
- C. NTFS
- D. All of the above a volume types in Windows 7.
Answer : D
You have a computer that runs Windows 7.
You need to view the processes that currently generate network activity.
What should you do?
- A. Open Resource Monitor and click the Network tab.
- B. Open Windows Task Manager and click the Networking tab.
- C. Open Event Viewer and examine the NetworkProfile Operational log.
- D. Open Performance Monitor and add all the counters for network interface.
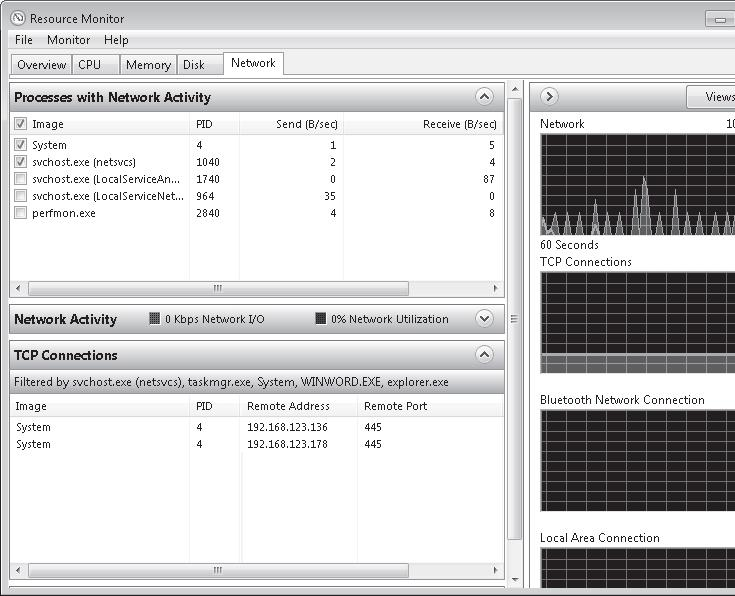
Answer : A
Explanation:
Resource Monitor -
Windows 7 offers an enhanced version of the Resource Monitor tool. Windows 7 Resource
Monitor allows you to view information about hardware and software resource use in real time. You can filter the results according to the processes or services that you want to monitor. You can also use Resource Monitor to start, stop, suspend, and resume processes and services, and to troubleshoot unresponsive applications. You can start
Resource Monitor from the Processes tab of Task Manager or by entering resmon in the
Search box on the Start menu. To identify the network address that a process is connected to, click the Network tab and then click the title bar of TCP Connections to expand the table. Locate the process whose network connection you want to identify. You can then determine the Remote Address and Remote Port columns to see which network address and port the process is connected to.
You have a wireless access point that is configured to use Advanced Encryption Standard
(AES) security. A pre-shared key is not configured on the wireless access point.
You need to connect a computer that runs Windows 7 to the wireless access point.
Which security setting should you select for the wireless connection?
- A. 802.1x
- B. WPA-Personal
- C. WPA2-Enterprise
- D. WPA2-Personal
Answer : C
Explanation:
WPA and WPA2 indicate compliance with the security protocol created by the Wi-Fi
Alliance to secure wireless computer networks. WPA2 enhances WPA, which in turn addresses weaknesses in the previous system, WEP. WPA was intended as an intermediate measure to take the place of WEP while an IEEE 802.11i standard was prepared. 802.1X provides port-based authentication, which involves communications between a supplicant (a client computer), an authenticator (a wired Ethernet switch or
WAP), and an authentication server (typically a Remote Authentication Dial In User
Service, or RADIUS, server).
WPA2-Enterprise -
WPA-Enterprise and WPA2-Enterprise authenticate through the Extensible Authentication
Protocol (EAP) and require computer security certificates rather than PSKs. The following
EAP types are included in the certification program:
- EAP-TLS
- EAP-TTLS/MSCHAPv2
- PEAPv0/EAP-MSCHAPv2
- PEAPv1/EAP-GTC
- EAP-SIM
If you want to use AES and to use computer certificates rather than a PSK, you would choose WPA2- Enterprise.WPA2-PersonalIf you have a small network that is not in a domain and cannot access a CA server, but you install a modernWAP that supports AES, you would use WPA2-Personal (with a PSK).WPA-Personal
If you have a small network that is not in a domain and cannot access a CA server and your WAP does not support AES, you would use WPA-Personal.802.1x
If you have a RADIUS server on your network to act as an authentication server and you want the highest possible level of security, you would choose 802.1X.
Which of the following is true of Windows 7?
- A. MailCentral is included as the new default mail client with Windows 7.
- B. Outlook Express is included with Windows 7.
- C. Microsoft Outlook is included with Windows 7.
- D. There is no preinstalled mail client included with Windows 7.
Answer : D
You have a computer that runs Windows 7.
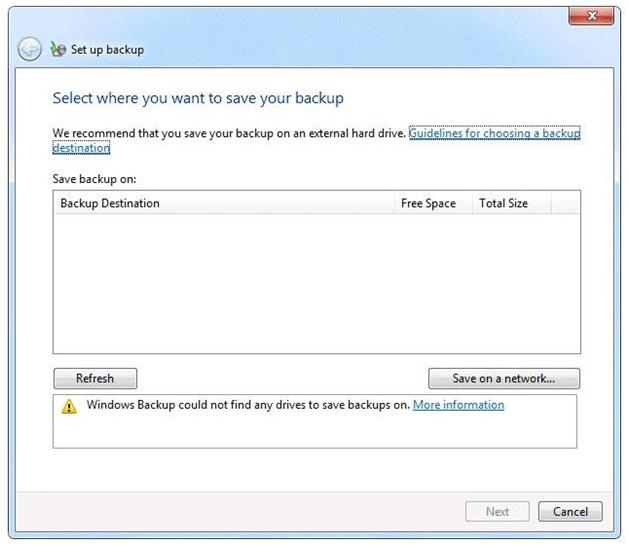
You run the Configure Backup wizard as shown in the exhibit. (Click the Exhibit button.)
You need to ensure that you can back up the computer to a local disk drive. What should you do before you run the Configure Backup wizard?
- A. Connect a removable disk.
- B. Log on as an administrator.
- C. Start the Volume Shadow Copy Service (VSS).
- D. Add your user account to the Backup Operators group.
Answer : A
Explanation:
An external hard drive External hard drives can be removed and stored in a secure location. However, they are typically slower than internal hard drives and tend to be less reliable, mainly because they are by default formatted using FAT rather than NTFS. You cannot use an external hard drive for a System Image backup unless you convert its filing system to NTFS. Because it is easily removable, it is more likely that an external hard drive will be missing when a scheduled backup is required. (Local disk drive was specified, not internal)NOT AdministratorYou need administrator credentials to configure scheduled backups or to manually initiate a backup. However, restoring files does not require administrator privileges unless a user attempts to restore another users file. (NOTE: The issue was a lack of location to store the Backup, not being about to run the Configure
Backup, thus it was assumed that the user in this scenario had administrator credentials)NOT Backup OperatorsMembers of this group are able to override file and folder access restrictions for the purpose of backing up data. You can allow a user to back up files and directories by assigning them to the Backup Operators group rather than by modifying the Back Up Files and Directories policy.NOT VSSVSS is installed on computers running Windows 7. Its startup type is Manual. The service starts as needed. If the service does not start when required, shadow copies are unavailable for backup and Windows
Backup does not succeed. Nor can you create restore points and previous versions. In this case, check the service and ensure that it has not been disabled.
You manage a computer that runs Windows 7.
You are tasked to identify which applications were installed during the last week.
What Windows component would you use to find this information? Choose two.
- A. Check the Windows System Change Log in the Control Panel.
- B. View the events in the Applications Log under Windows Logs in the System and Security component section of the Control Panel.
- C. The informational events should be reviewed from Reliability Monitor.
- D. Check the Windows System Diagnostics Report under the Performance Monitor MMC.
Answer : B,C
Which of the following utilities can you use to transfer user encryption certificates from a computer running Windows XP Professional to Windows 7 Professional? Choose two.
- A. File Settings and Transfer Wizard
- B. USMT
- C. Windows Easy Transfer
- D. Robocopy.exe
Answer : B,C
You have a computer that runs Windows 7 Professional. A USB disk is attached to the computer.
You need to ensure that you can enable BitLocker to go on the USB disk.
What should you do?
- A. Enable Encrypting File System (EFS).
- B. Upgrade the computer to Windows 7 Enterprise.
- C. Initialize the Trusted Platform Module (TPM) hardware.
- D. Obtain a client certificate from an enterprise certification authority (CA).
Answer : B
Explanation:
Windows 7 ProfessionalWindows 7 Professional is available from retailers and on new computers installed by manufacturers. It supports all the features available in Windows
Home Premium, but you can join computers with this operating system installed to a domain. It supports EFS and Remote Desktop Host but does not support enterprise features such as AppLocker, DirectAccess, BitLocker, and BranchCache.Windows 7
Enterprise and Ultimate EditionsThe Windows 7 Enterprise and Ultimate editions are identical except for the fact that Windows 7 Enterprise is available only to Microsofts volume licensing customers, and Windows 7 Ultimate is available from retailers and on new computers installed by manufacturers. The Enterprise and Ultimate editions support all the features available in other Windows 7 editions but also support all the enterprise features such as EFS, Remote Desktop Host, AppLocker, DirectAccess, BitLocker, BranchCache, and Boot from VHD.
You have a computer that runs Windows 7. The computer has System Protection enabled.
You need to retain only the last System Protection snapshot of the computer. All other snapshots must be deleted.
What should you do?
- A. Run Disk Cleanup for Programs and features.
- B. Run Disk Cleanup for System Restore and Shadow Copies.
- C. From the System Protection Restore settings, select Turn off System Restore.
- D. From the System Protection Restore settings, select Only restore previous versions of files.
Answer : B
Explanation:
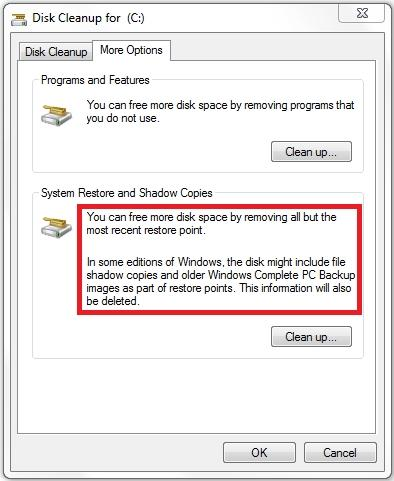
Shadow info:
Shadow copies are automatically saved as part of a restore point. If system protection is enabled, Windows 7 automatically creates shadow copies of files that have been modified since the last restore point was created. By default, new restore points are created every seven days or whenever a significant system change (such as a driver or application installation) occurs.
Which of the following best describes how the user is alerted with information system and configuration alerts?
- A. A popup occurs and the Windows 7 desktop contrast is dimmed. Until you acknowledge the alert the screen will not move.
- B. If Aero is installed the shaking alert flag appears in the index bar of every open window.
- C. A flag in the taskbar with a red "x" indicates there is a problem needing attention.
- D. All of the above
Answer : C
Your network contains 100 computers that run Windows XP.
You need to identify which applications installed on all of the computers can run on
Windows 7.
You must achieve this goal by using the minimum amount of administrative effort.
What should you install?
- A. Microsoft Application Compatibility Toolkit (ACT)
- B. Microsoft Assessment and Planning (MAP) Toolkit
- C. Microsoft Deployment Toolkit (MDT)
- D. Windows Automated Installation Kit (AIK)
Answer : A
Explanation:
The Microsoft Application Compatibility Toolkit (ACT) 5.6 enables software developers, independent software vendors (ISVs), and IT professionals who work in a corporate environment to determine, before deployment within the organization, whether their applications are compatible with a new version of the Windows operating system. ACT also enables such individuals to determine how an update to the new version will affect their applications.
You can use the ACT features to:
- Verify your application's, device's, and computer's compatibility with a new version of the
Windows operating system, including determining your risk assessment.
- Verify a Windows update's compatibility, including determining your risk assessment.
- Become involved in the ACT Community, including sharing your application assessment with other ACT users.
- Test your applications for issues related to User Account Control (UAC) by using the
Standard User Analyzer (SUA) tool.
- Test your Web applications and Web sites for compatibility with new releases and security updates to Internet Explorer, by using the Internet Explorer Compatibility Test Tool.

